Actionable Intelligence that Stops You Drowning in Vulnerabilities
Move past overwhelming vulnerability backlogs, alert fatigue and decentralized spreadsheets. Get the 1% of CVEs that actually need action, backed by real-time intelligence from 1000+ sources.

Faster Alerts, Broader Threat Coverage, Less Resources

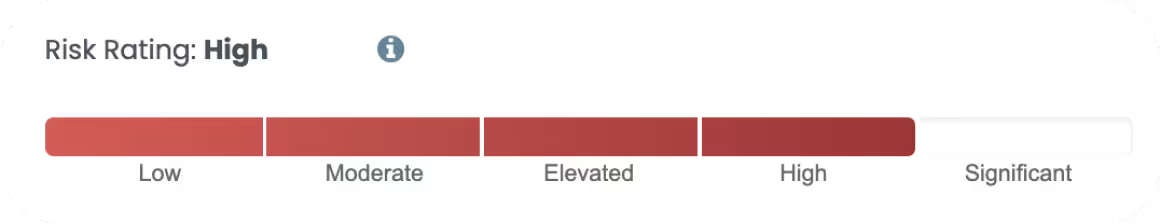
Risk Ratings Backed by the latest Intelligence
Rapidly identify the 1% of vulnerabilities that need immediate action.
Cytidel’s risk algorithm dynamically rates each vulnerabilitiy based on real-time intelligence.
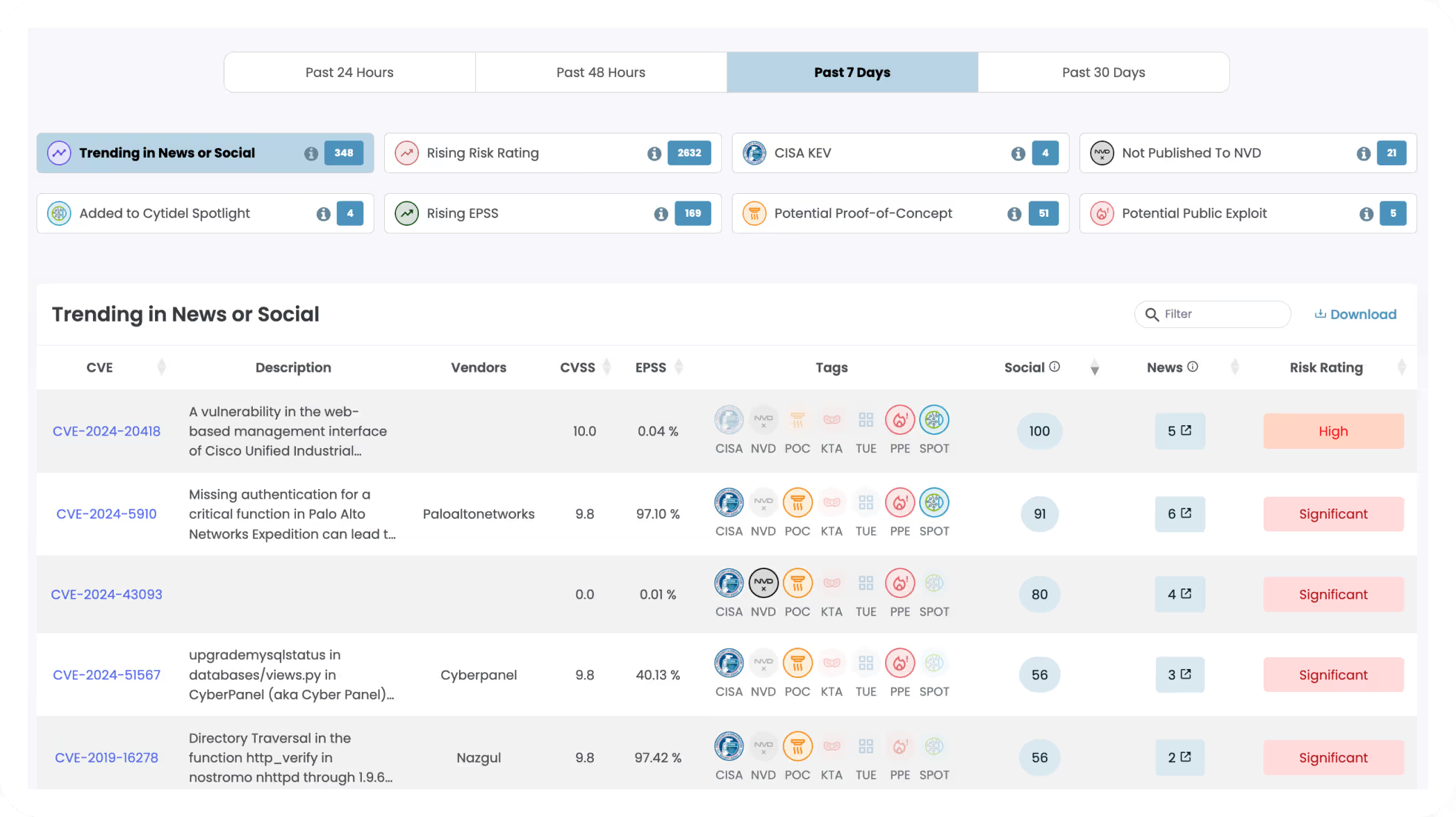
Real-time vulnerability Trends
Don’t wait for scanner updates or NVD entries — get insights when threats are just starting to trend.
Our data engine continuously monitors thousands of sources, alerting you to vulnerabilities gaining traction across the threat landscape.



Custom Alerting tailored to your needs
Set custom alerts based on keywords, vendors, or criteria you care about most.
Receive real-time notifications on threats that impact your environment, so you’re always prepared for the latest risks.
Threat Actor Database
Gain deeper context on the adversaries targeting your industry.
Cytidel’s Threat Actor Database allows you to search for known threat actors, their aliases, and instantly see all linked vulnerabilities associated with their tactics.


"I'm enjoying a cup of tea and a break because of the speed and accuracy of your work which repeatedly keeps me ahead of the threats and the news-cycle.
I personally recommend that everyone in my network, whether your a VP, director, or a manager like me, should check out Cytidel"
See what others are saying.
We’ve designed our solutions to help overcome the key challenges facing threat and vulnerability management teams
“I have three things I love to talk about. My wife, my kids, and now Cytidel”
“Cytidel’s data collection is better than anything else I’ve seen on the market”
“Their threat intelligence capability and implementation is the best I have seen”
“This gives me the reassurance that I know I’m not missing something huge in the community”
"Time and time again Cytidel speeds up my day, saves me time and in doing so saves on budget and resources!. They are making a real impact over here.
“Working with Cytidel has helped us rank and prioritise what to do next. They are passionate about information security, and it shows in the effective work they do.”

frequently Asked Questions
These FAQs should help clarify how our platform can streamline and enhance your Threat And vulnerability management capabilities
Why is prioritising by CVSS not enough?
CVSS gives you a fixed score that measures the potential impact of a vulnerability, but in reality the risk posed by vulnerabilities changes daily. This can overwhelm your team and result in a lot of unnecessary work, as the average enterprise is Prioritising 73% of vulnerabilities for remediation when using CVSS score to rank risks. Cytidel uses dynamic risk ratings to keep your focus on the few vulnerabilities most likely to lead to a breach, while clearing lower risk vulnerabilities off your to-do list.
What sources do Cytidel monitor?
We monitor thousands of trusted sources across news, social media, vendor advisories, exploit repositories, and more. Whether you’re looking for celebrity vulnerabilities, or interested in the latest emerging zero-day vulnerabilities, we’ve got you covered. No more FOMO, no more switching between multiple platforms or endless scrolling - just log into the Cytidel platform and catch up on all the news you need to know.
How does Cytidel’s Risk Rating work?
Our risk rating is our secret sauce! We evaluate both new and existing vulnerabilities based on factors like threat scores, trending vulnerabilities, exploitation evidence, and threat intelligence prominence.
Can the risk rating be tailored to my organisation?
Cytidel’s risk rating is the cornerstone of your vulnerability ranking strategy, enabling you to rank vulnerabilities and remediate the risks that matter most to your organisation. While our default risk rating has been extensively tested to cater for most organisations starting out on their adoption of risk-based vulnerability management, some organisations want to tailor this to suit their risk tolerance levels and specific needs. Tailored risk ranking processes can be accommodated on our Enterprise plan. Our expert team are on hand to discuss your needs and support you in designing the workflow that works best for you.
Does Cytidel integrate with my tools or provide API access?
Cytidel’s vulnerability intelligence and risk ranking platform as a web-based SaaS portal allowing you to monitor the latest emerging risks. For customers on an Enterprise plan, our API can be made available. Custom integrations with your existing vulnerability scanning tools are available with a custom deployment designed specifically to suit your needs and integrate with your existing tech stack. Talk to a member of our team about how we can streamline your threat intelligence gathering and automate your vulnerability ranking processes.
Are Cytidel ISO27001:2022 certified?
Yes, we are! This certification reflects our commitment to the highest standards of information security and safeguarding our customers' data. We’ve also designed our platform to help organisations undergoing an ISO27001 assessment by automating intelligence gathering, analysing vulnerability trends, and providing tools to match scans against the latest threat intelligence - all tailored to your needs. Check out our blogpost on what’ve learnt in the process here.
Do I need to give Cytidel access to my data to get the benefits of the platform?
No, this isn’t mandatory. Our founders have decades of experience working in complex enterprise environments and understand the challenges of integrating new technologies. Cytidel was designed specifically to sit on top of your tech stack and allow you to get immediate value from the platform without the need to ingest and analyse your internal security data. When you’re ready to start integrating and automating processes, we’re here to help.
How does onboarding work?
While we believe we have made the Cytidel platform intuitive and easy to use, it is still a specialised product. This is why we recommend going with a demo to kick things off, after which we can either add you to a trial with a clear success plan, or get you and your team onboarded straight away. Account creation and registration takes just a few minutes, plus we have Stripe fully integrated into our portal for simple billing.
I don’t know if we’re ready for this. Is there something we can do first?
Don’t worry, you’re not alone here! Our founders built Cytidel because they found themselves regularly supporting clients who were still prioritising by CVSS, were overwhelmed with the volume of vulnerabilities, and didn’t know where to turn. If you want a member of the Cytidel team to guide you through the platform and help you get value from day 1, we’re more than happy to support you through a trial.
1000+ sources distilled into one simple, actionable view
Enhance your threat and vulnerability management capabilities with Cytidel. Thousands of intelligence sources vetted, analysed and mapped against CVEs in real-time












+ 1000 more




